Absolute Software Corporation's product "Absolute Home & Office" formerly known as "CompuTrace" is a combined software and firmware component included with many modern laptops and desktops. High-end and business machines are more likely to include this feature. The purpose of the product is to discourage theft of laptop and desktop computers and aid in recovery in the event the device misplaced or stolen. The feature is inactive by default on new machines and remains that way unless activated. Activation and usage is done through the Absolute Software console and requires a subscription. The software has two parts, the component that runs within the Windows operating system and the firmware component embedded in the system BIOS or UEFI. Once activated, the agent is installed within the Windows operating system on the machine, it is not compatible with any other operating systems such as Linux. The Windows agent performs all of the primary functions of the software including communication with Absolute Software servers and anti-theft measures such as remote wipe, device lock down, location tracking, etc. There are other software products such as Prey that provide similar functionality. What makes Absolute's solution unique is the firmware component. Absolute software has obtained agreements with several popular personal and business computer manufacturers including HP, Dell, Lenovo, Acer, ASUS, Toshiba and more to have their software built into the BIOS or UEFI firmware of the machine. The "persistence module" in the system firmware (when activated) is responsible for re-installing the Windows agent in the event the system drive is wiped or replaced. This is to further combat the reuse of the machine after theft. In most cases installing a new hard drive or SSD or just formatting the existing one followed by installing a fresh copy of Windows would remove all security software and measures installed on the system, making it clean and usable again. This is not the case when Absolute / CompuTrace is active on the machine. As soon as an unmodified copy of Windows 7 or newer is installed and booted up, the persistence module from the system firmware copies an executable called rpcnetp.exe to C:\Windows\System32 which is then used to re-install the Windows agent. This agent connects to Absolute servers and downloads additional program components once the machine connects to the Internet. If the machine is flagged as lost or stolen, it may be locked or a remote wipe may be automatically performed. Installing Linux or never connecting the machine to the Internet are pretty much the only ways around it at this point.
The issue with Absolute / CompuTrace is the extreme similarity to multiple types of computer malware based on its design and behavior. First, it qualifies as a rootkit because it injects itself at very low levels into the operating system and can even persist through drive wipes or replacement due to its firmware component. It also qualifies as a Trojan due to its communication with Absolute servers (command and control servers) and its ability to automatically install new modules and change system parameters all completely transparent to the user. There is no doubt Absolute Software has many happy customers and certain organizations benefit from the product, but it does pose a security and privacy risk if someone unknowingly purchases a second-hand system with the software activated. Additionally, something doesn't sit right with us knowing Absolute Software has extremely persistent and high level of access into millions of computers. The agent itself has already been exploited within the local network, think about the possible consequences if Absolute Software were to be compromised. The full Absolute / CompuTrace executable is called rpcnet.exe and also runs as a service. This is downloaded by rpcnetp.exe and used primarily for all other functions.
There is a solution! Keep reading if you are interested, but be aware this will NOT work if your machine has been marked as stolen! If you purchased a stolen machine, get in touch with the seller and sent it back immediately, and if you stole the machine, you need to re-evaluate your life choices. If you've legitimately obtained a laptop or desktop second-hand, you can do the following to check and see if your machine even supports CompuTrace / Absolute Persistence and if so, whether it's active or inactive. Enter your system's BIOS or UEFI setup by rebooting it and pressing the manufacturer-specific key (F10 for HP and F12 for Dell). On an HP machine it will be under the security tab towards the bottom and likely within the "Anti Theft" menu. On a Dell system it usually has its own category. For other brands, it varies, so you will just have to look around. Below is a screenshot from an HP system. If you find no record of Absolute Persistence / CompuTrace in your BIOS, your machine likely doesn't support it and you don't need to continue!
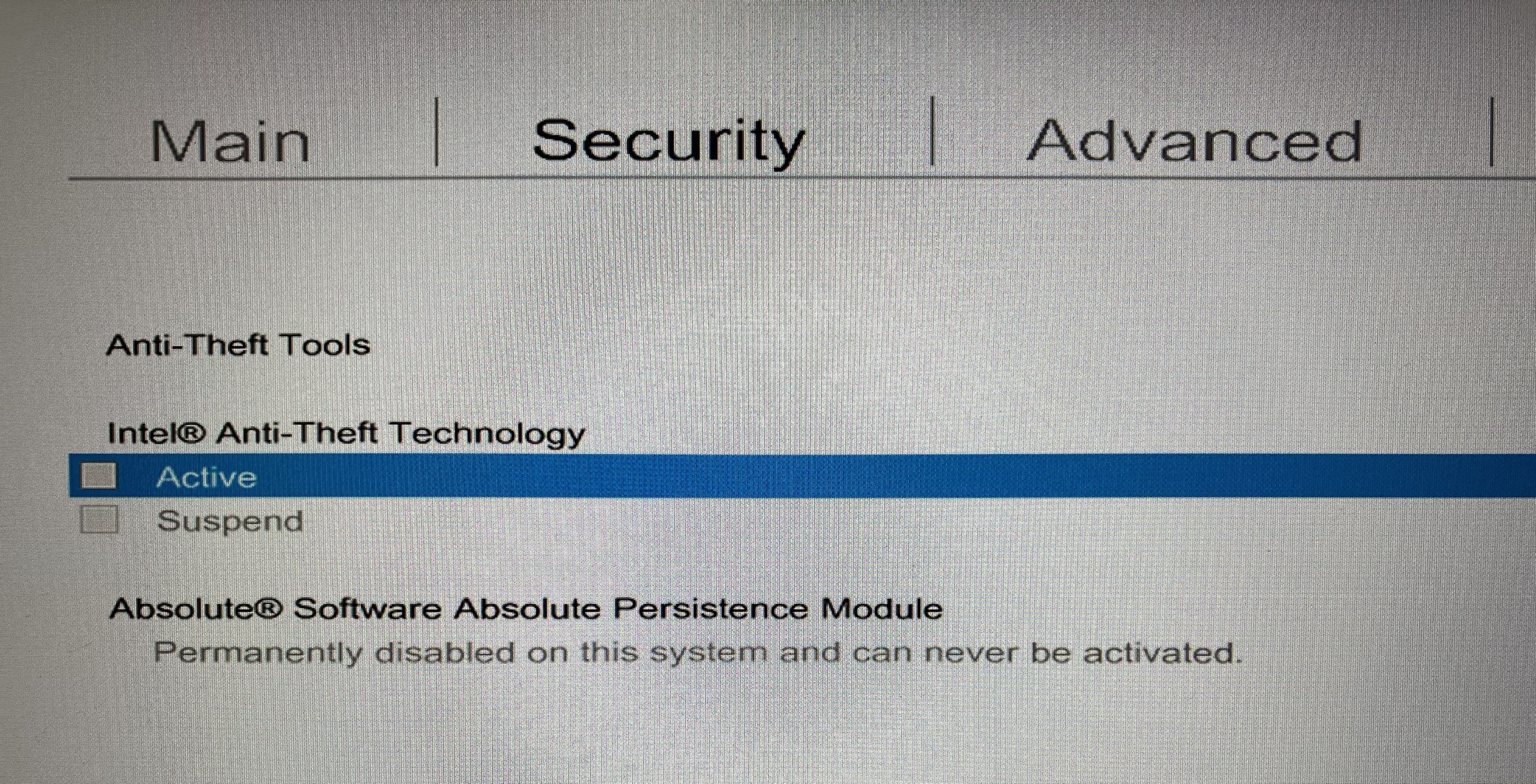
CompuTrace / Absolute Persistence has 3 possible states:
Inactive - persistence is currently disabled but can be enabled by obtaining a subscription and registering your device by the serial number
Active - persistence is active, either bound to an active subscription or has not yet contacted Absolute servers after being decommissioned
Permanent disable - persistence module is permanently blocked and cannot be re-enabled (even by a BIOS flash)
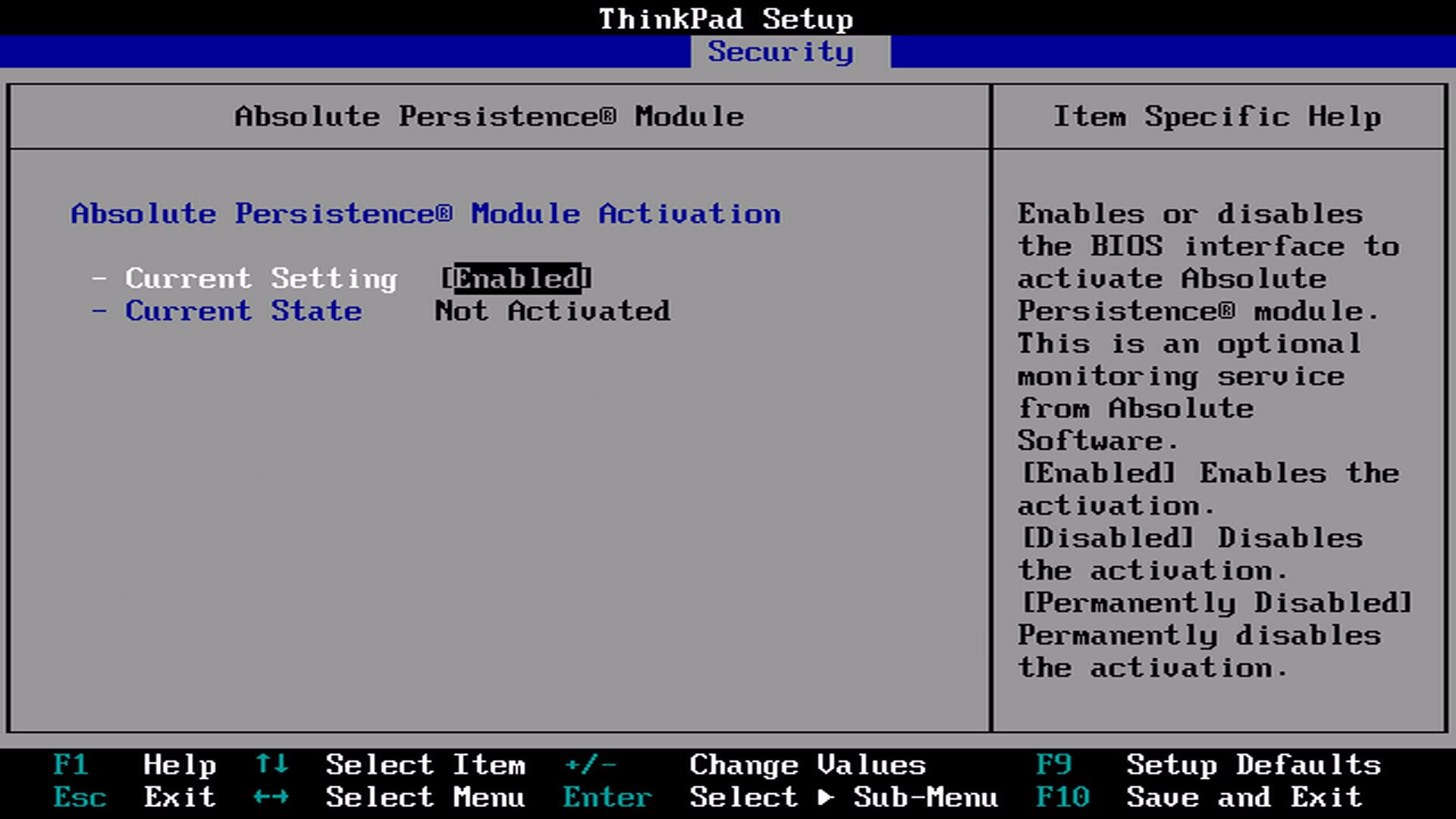
Your machine will most likely be in the "inactive" state which means you can continue. If your machine is in the "active" state you will need to do the following: ensure your machine is NOT stolen, and contact Absolute software by email and provide your system serial number. Their support is friendly and they will verify your serial with the previous owner or organization to confirm the machine has been decommissioned. Once they reach back out and confirm the machine has been decommissioned, you will need to install Windows on your machine if it's not already and leave it connected to the Internet for up to 48 hours (it usually only takes a couple of hours). What will happen is the agent software will communicate with Absolute servers and obtain the updated decommissioned status, then the persistence module will be switched to the "inactive" state and the BIOS will reflect this change. Below is a screenshot from a Lenovo system.
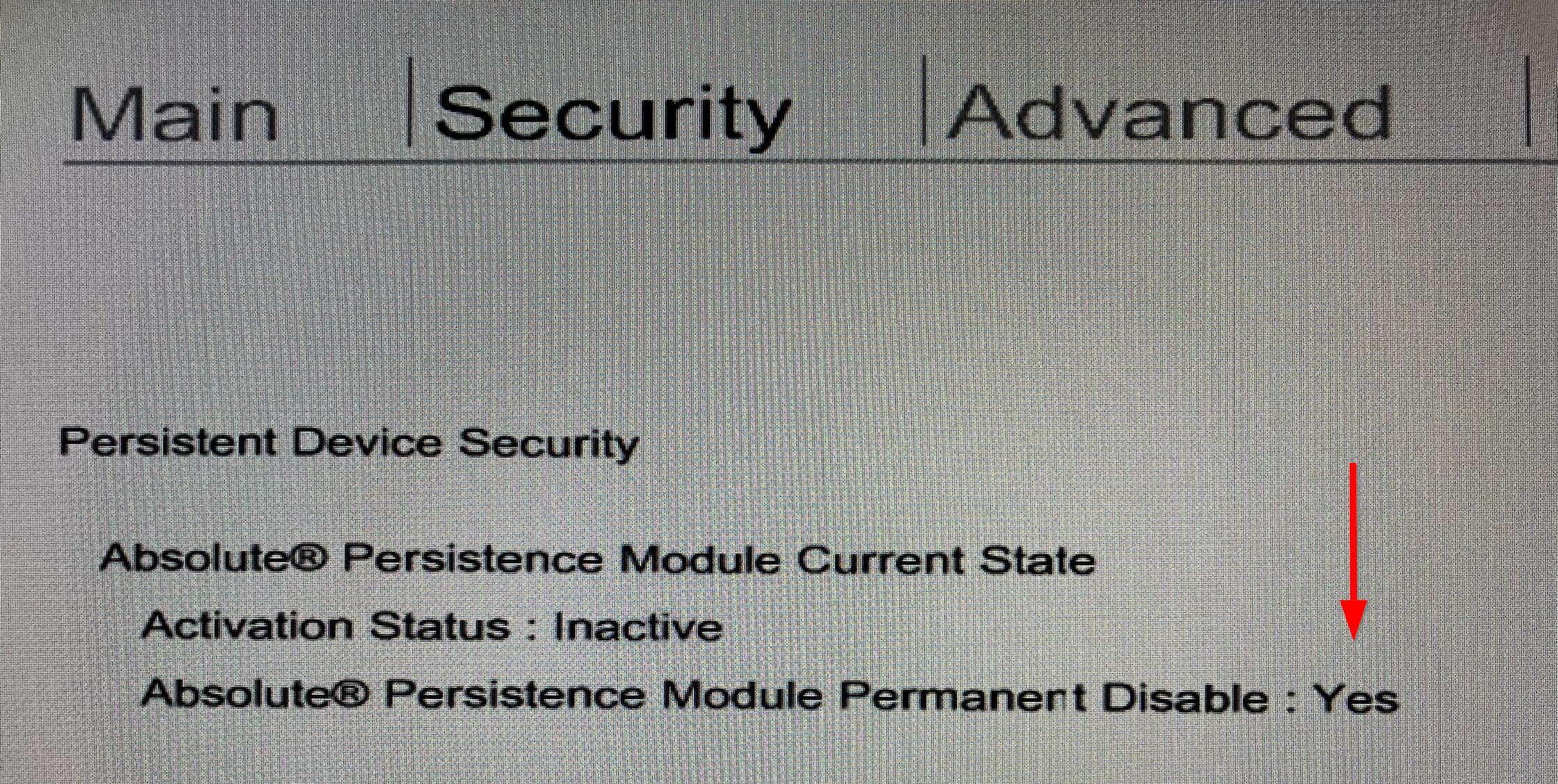
Once the status of Absolute Persistence is "inactive" you can proceed to permanently disable the feature. It is not strictly necessary to do this, as when inactive it does not do anything, but if you are concerned about security and don't intend to ever use the product, why not kill it! After all, there is a reason why "permanent disable" is a choice. On Dell systems and most others, all you have to do is change the status to "permanent disable" by selecting it and saving changes in the BIOS or UEFI setup. However, HP systems make this slightly more complicated. In the HP BIOS setup utility, there is an entry for "Absolute Persistence module permanent Disable" under Persistence Module Current State. In most cases, this will read "No" unless someone else has already completed this process on the machine, which is extremely unlikely. Unlike Dell and other manufacturers, there isn't a way to change this from the BIOS setup screen. Instead, you actually have to do it from within Windows using the HP Bios Config Utility (BCU) or the Client Management Script Library for PowerShell. It is unclear why HP adds this extra step when other manufacturers let you disable it right in the BIOS setup but we assume it is to prevent someone from unknowingly executing an irreversible action and then complaining to HP support.
We recommend using the HP Client Management Script Library for Windows PowerShell. It is surprisingly easy to use and intended to replace the HP Bios Config Utility (BCU) which has been deprecated. Start by downloading the Client Management Script Library from the HP website, then install it and open up a PowerShell window as administrator. Issue the following commands to first check whether Absolute Persistence is active or inactive, and then execute the permanent disable operation. Remember, there is no going back from here!
- PS C:\Windows\System32> Get-HPBIOSSetting -Name "Absolute Persistence Module Current State"
- PS C:\Windows\System32> Set-HPBIOSSettingValue -Name "Permanent Disable Absolute Persistence Module Set Once" -Value "Yes"
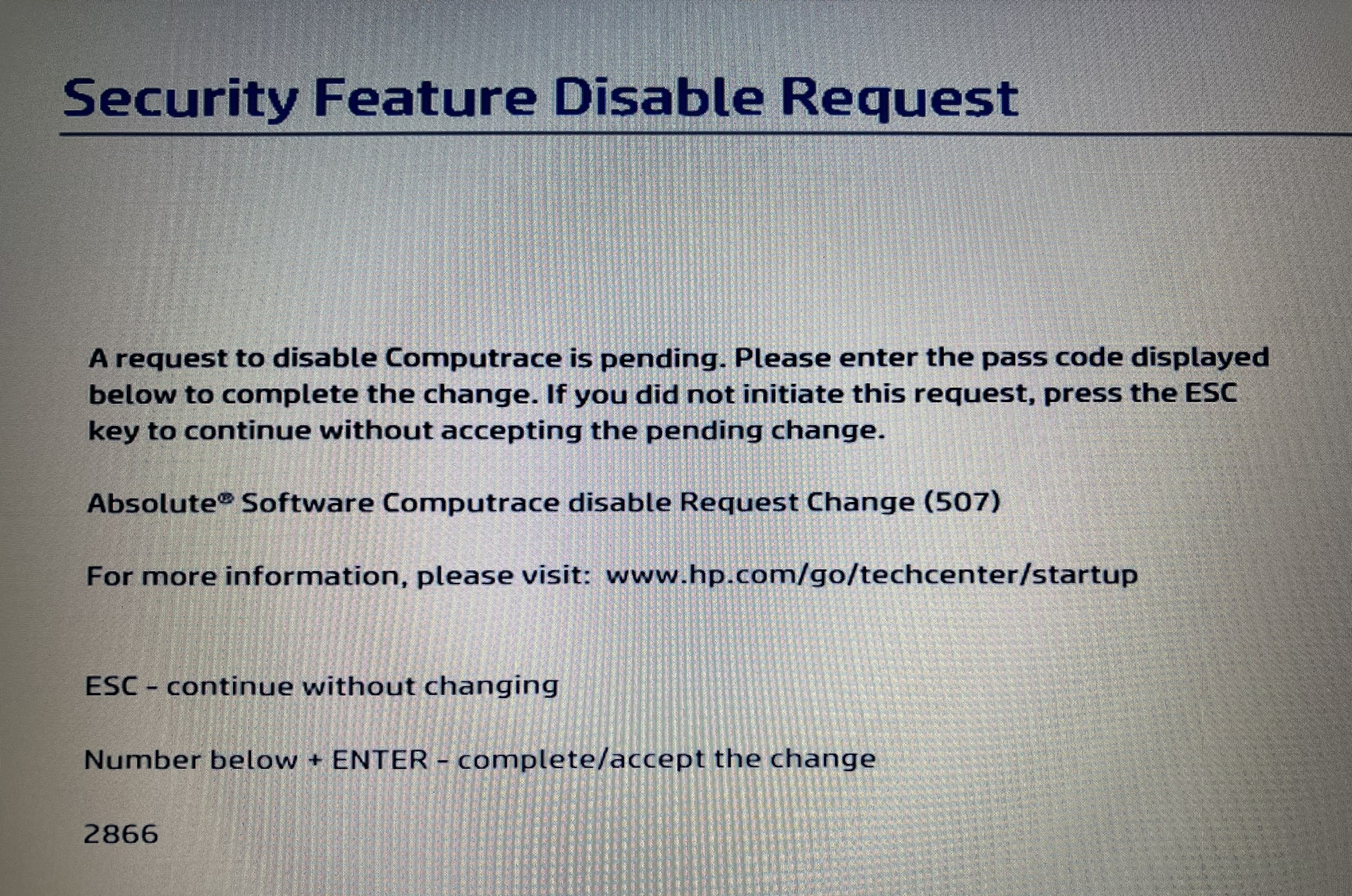
Once you have successfully executed the permanent disable command, you need to reboot your system. If the command fails, it is likely due to one of the following reasons: you have not properly installed the HP CMSL, your machine does not have Absolute Persistence built into the firmware, or your system has a BIOS admin password set. If your system has a BIOS admin password you either need to temporarily disable it or use HpqPswd.exe in conjunction with -Password to pass the admin password through when executing the command. You will know you have reached success when you reboot your machine and receive the following screen. This verification screen is part of the HP Physical Presence Interface (PPI). The sole purpose is to ensure a human sitting at the keyboard confirms or denies security and firmware-level changes. This is to prevent malicious programs from easily being able to disable firmware security features. The PPI can be disabled by a BIOS setting but that is out of the scope of this writeup.
Finally, after passing the PPI, you can enter the system BIOS or UEFI setup to confirm that CompuTrace / Absolute Persistence has been permanently disabled!
Below are some links you may find useful after reading this writeup